

This article is primarily intended to assist employees with the setup and use of MFA (Multi-Factor Authentication) with their Microsoft account. The topics covered include:
- What is MFA (Multi-Factor Authentication)
- Why use MFA
- Who should use MFA?
- Setup of MFA with a Microsoft account
- Pros and Cons of Authentication Methods
- Additional security measures
What is MFA (Multi-Factor Authentication)
MFA is a layered process to confirm the user logging in is in fact who they say they are. Two-Part Authentication is a form of MFA and you might hear MFA referred to as Secure Verification.
MFA is a combination of at least 2 of the following:
- Something you know – like a Password
- Something you have – Phone, USB Key, App, Text message
- Something you are - biometrics (fingerprint, facial recognition, iris scan, etc)
Why use MFA
The process of authentication with just a username and password has been proven over and over to be a very weak level of security. At Overlake, we have a responsibility to protect our accounts, our identities, our school’s reputation, and our community’s information, which are just a few reasons to take additional measures to be more secure. Many organizations have suffered great losses due to compromised usernames and passwords. Daily hackers around the world on a daily basis are using applications that keep improving to ‘crack’ passwords with ever-growing success.
Who should use MFA?
All employees at Overlake should be using MFA. Students can contact the Tech department if they wish to have MFA enabled for their account.
Setup MFA with a Microsoft account
When initially getting set up with MFA, Overlake Faculty and Staff will need to choose the method of MFA they wish to use. The MFA methods to choose between are the mobile phone app called Microsoft Authenticator, or a USB Key (aka dongle).
The phone app, “Microsoft Authenticator”, can be installed from either the App Store or the Play Store for free. This link will offer a QR code to scan and easily install Microsoft Authenticator
In the Store, be careful to select Microsoft Authenticator. In the Apple App Store, you might be required to log in with your Apple ID and password.
If a Faculty or Staff member selects to use a USB Key for authentication, the Key will be issued by the Tech department and is either USB-C (small oval) or USB-A (rectangular).
To help with the decision of which Authentication method to use please consider the
Pros and Cons of Authentication Methods:
 Phone App
Phone App
+ Usually nearby
+ Quick Notification approval
+ Doesn’t require another piece of hardware to keep on hand
- Use of a personal device
* An insignificant amount of space is used on phone (158mb)
 USB Key (C or A)
USB Key (C or A)
+ Doesn’t require the use of a personal device
- inserting the device into the laptop
- creation/remembering another PIN
Once an Authentication method has been decided, the next step, in conjunction with the Tech department, is to add the method in the Microsoft account Security Info.
Use MS Security info to manage Authentication Methods
To add an authentication method for first use or if you need to change a method, perhaps since a new phone or new USB Key is in use, the following steps should help:
Sign in at https://Office.com then click the user profile in the upper-right corner.
Next View account, on Security info, click UPDATE INFO >
Here is a direct link to Microsoft Security Info - https://mysignins.microsoft.com/security-info
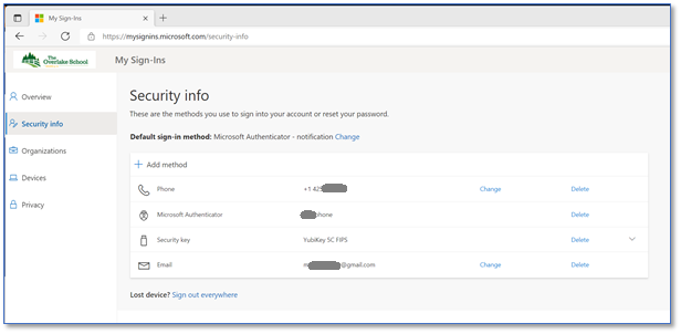
Once signed-in, authentication methods can be managed via Security info
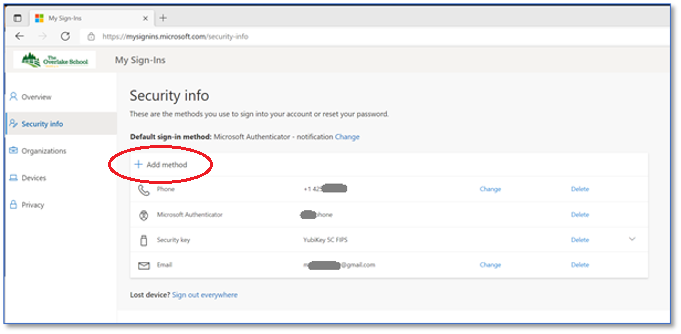
 Click the " + Add Method " to add either the Authenticator App or Security Key
Click the " + Add Method " to add either the Authenticator App or Security Key
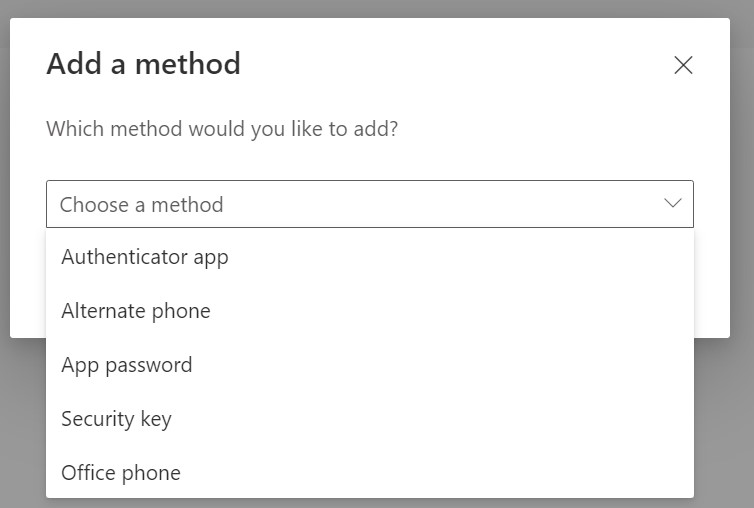
 Select the desired option and follow the prompts as directed.
Select the desired option and follow the prompts as directed.
Additional Security Measures
Practicing good computing security measures in your personal life is just as important as it is at work. Here are some suggested additional security measures:
Use a Password Manager
A password manager can remember the many passwords, generate unique, complex passwords, warn of duplicate use, etc. Consider using one of these Password Managers:
Use biometrics to login (Facial recognition, fingerprint, etc)
Use MFA or 2 Factor everywhere possible at home and work. For example:
- Personal Email
- Internet Service Provider
- Cloud Storage
- Anywhere possible!
Lock your Screen on laptop (Windows users can press the Window key + L ) or phone when you step away.
Do not leave a laptop or laptop bag visible in a vehicle.